Compare
A More Effective Approach Than Cloudflare Page Shield
Looking to secure your site against malicious third-party scripts? Let us show you how!
What you will learn
Why we're different
How c/side compares against Cloudflare Page Shield
c/side offers greater protection at a lower cost. Check our pricing
c/side’s independently QSA audited PCI dashboard automates the tedious tasks that eat up your team's hours while providing real-time protection against javascript-based attacks on payment pages.
c/side | ||||
|---|---|---|---|---|
| Criteria | Why It Matters | What the Consequences Are | ||
| Approaches used | Proxy + agent based detections but also offers crawler and offers a free CSP reporting endpoint | CSP + fetching script after | ||
| Real-time Protection | Attacks can occur between scans or in the excluded data when sampled | Delayed detection = active data breaches | ||
| Full Payload Analysis | Ensures deep visibility into malicious behaviors within script code itself | Threats go unnoticed unless the source is known on a threat feed | ||
| Dynamic Threat Detection | Identifies attacks that change based on user, time, or location | Missed detection of targeted attacks | ||
| DOM-Level Threat Detection | Tracks changes to the DOM and observes how scripts behave during runtime | Unable to identify sophisticated DOM-based attacks | ||
| 100% Historical Tracking & Forensics | Needed for incident response, auditing, and compliance | Needed for incident response, auditing, and compliance | ||
| Bypass Protection | Stops attackers from circumventing controls via DOM obfuscation or evasion | Stealthy threats continue undetected | ||
| Certainty the Script Seen by User is Monitored | Aligns analysis with what actually executes in the browser | Gaps between what’s reviewed and what’s actually executed | ||
| AI-driven Script Analysis | Detects novel or evolving threats through behavior modeling | Reliance on manual updates, threat feeds or rules = slow and error-prone detection | ||
| QSA validated PCI dash | The most reliable way to ensure a solution is PCI compliant is to conduct a thorough audit by an independent QSA | Without QSA validation, you rely entirely on marketing claims, which could result in failing an audit | ||
| SOC 2 Type II | Shows consistent operational security controls over time | Lacks verified security control validation, making it a risky vendor | ||
| PCI specific UI | An easy interface for quick script review and justification via one click or AI automation | Mundane tasks and manual research on what all the scripts do, which takes hours or days |
Why c/side Succeeds Where Others Fail
Traditional security approaches face major limitations that bad actors leverage: content security policies (CSPs), crawlers and JavaScript agents. They may only detect clean scripts, slow down your website, or completely overlook dynamic threats that detonate for specific users, times, devices or locations.
c/side's Hybrid Proxy Advantage:
Real-time Protection
Inspects every script before it reaches users, with zero latency
Complete Visibility
Analyzes exactly what each visitor's browser executes
AI-Powered Analysis
Surfaces sophisticated threats that traditional tools miss
100% Historical Tracking
Records every script payload for rapid incident response
Dynamic Detection Catches
Detect targeted attacks that only occur for specific users, times, or locations
Bypass Protection
Defeats CSP evasion, shadow DOM tricks, and obfuscated code
Make PCI DSS 4.0.1 Easy
PCI DSS 4.0.1 requirements 6.4.3 and 11.6.1 compel businesses to protect client-side Javascript on their site (1st party, 3rd party and dependencies of 3rd parties). c/side takes care of you and continuously discovers and catalogs every script on your payment pages. When new scripts appear, AI generates business justifications automatically. Weekly audit reports are delivered to your inbox in PDF format, ready for QSA compliance reviews.
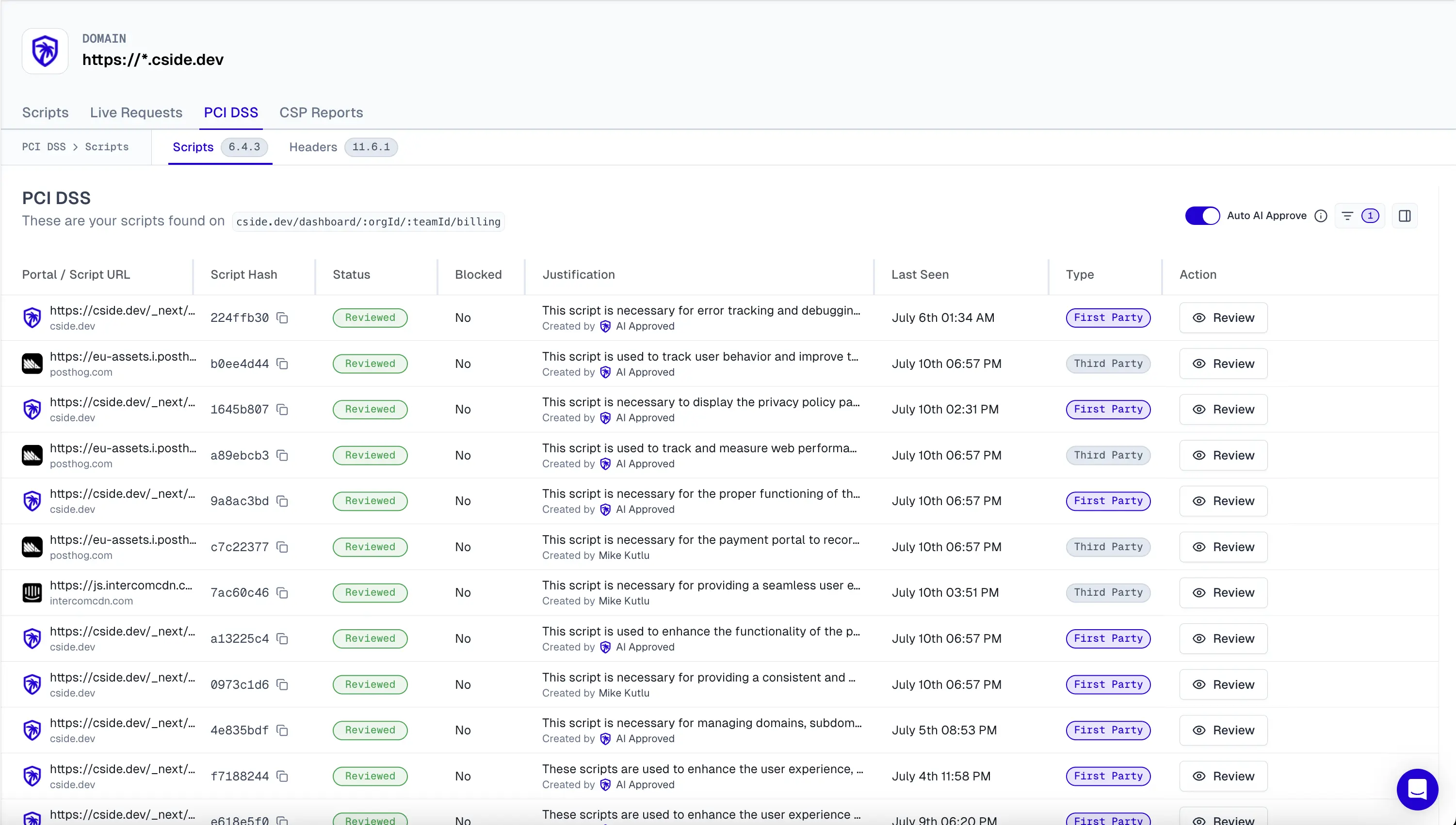
in image: cside PCI dashboard for scripts 6.4.3
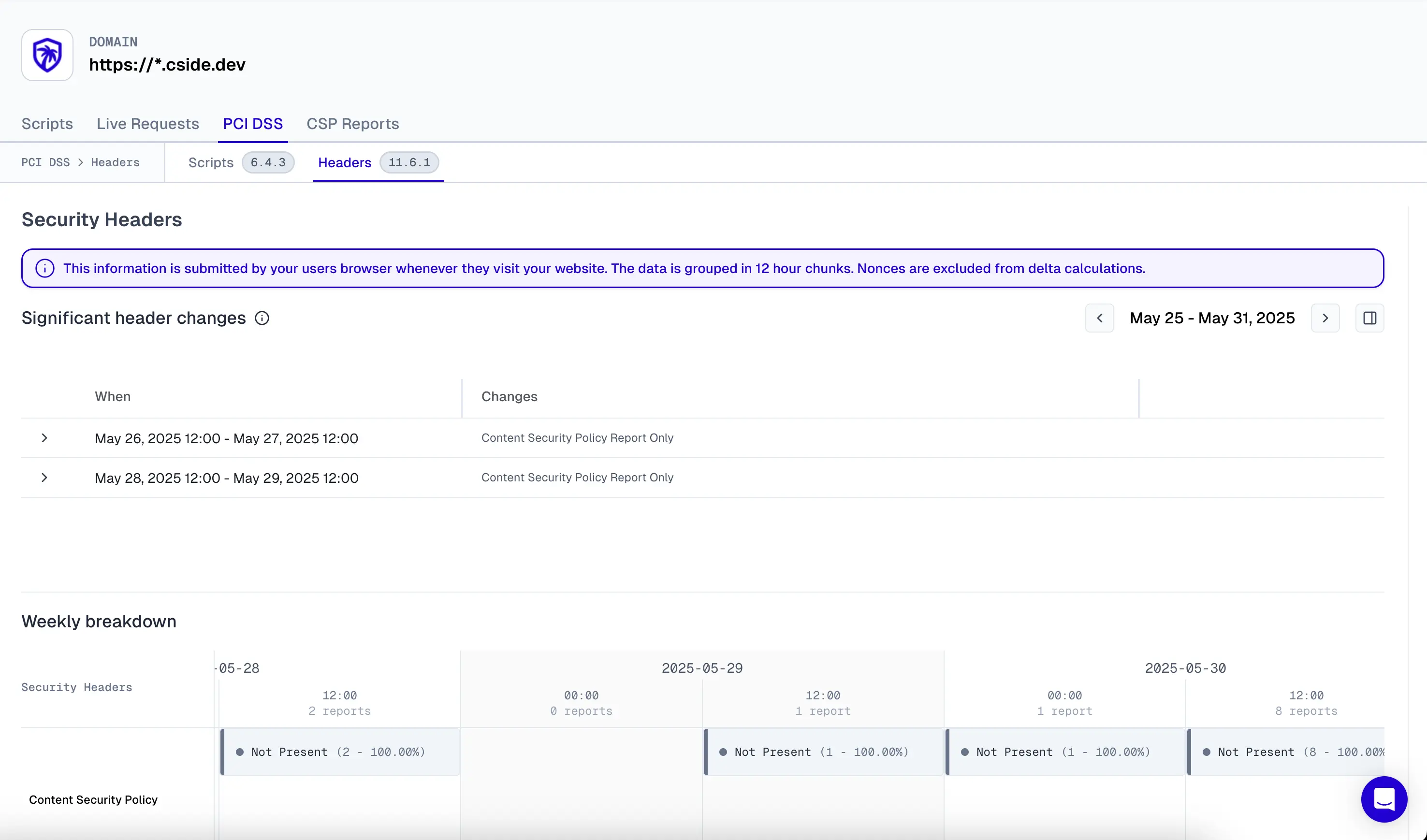
in image: cside PCI dashboard for headers 11.6.1
"Through this comparative analysis, VikingCloud observed that the proper implementation of the c/side platform effectively mitigates attacks specific to the scenarios targeted by PCI DSS requirements 6.4.3 and 11.6.1."
VikingCloud

380k+ compromised websites found in 2025
In 2025 alone, we found 380,000 compromised websites, highlighting a growing reliance by attackers on Javascript-based delivery mechanisms, third-party supply chain vulnerabilities, and deceptive social engineering tactics such as fake browser updates.
Why Leading QSAs Prefer c/side
Only c/side delivers
Contact us
Our friendly team would love to hear from you.
Frequently Asked Questions
Everything you need to know about the product.