Monitoring, Securing, Optimizing 3rd party scripts
Keeping track of 3rd party scripts, taking away obscurity
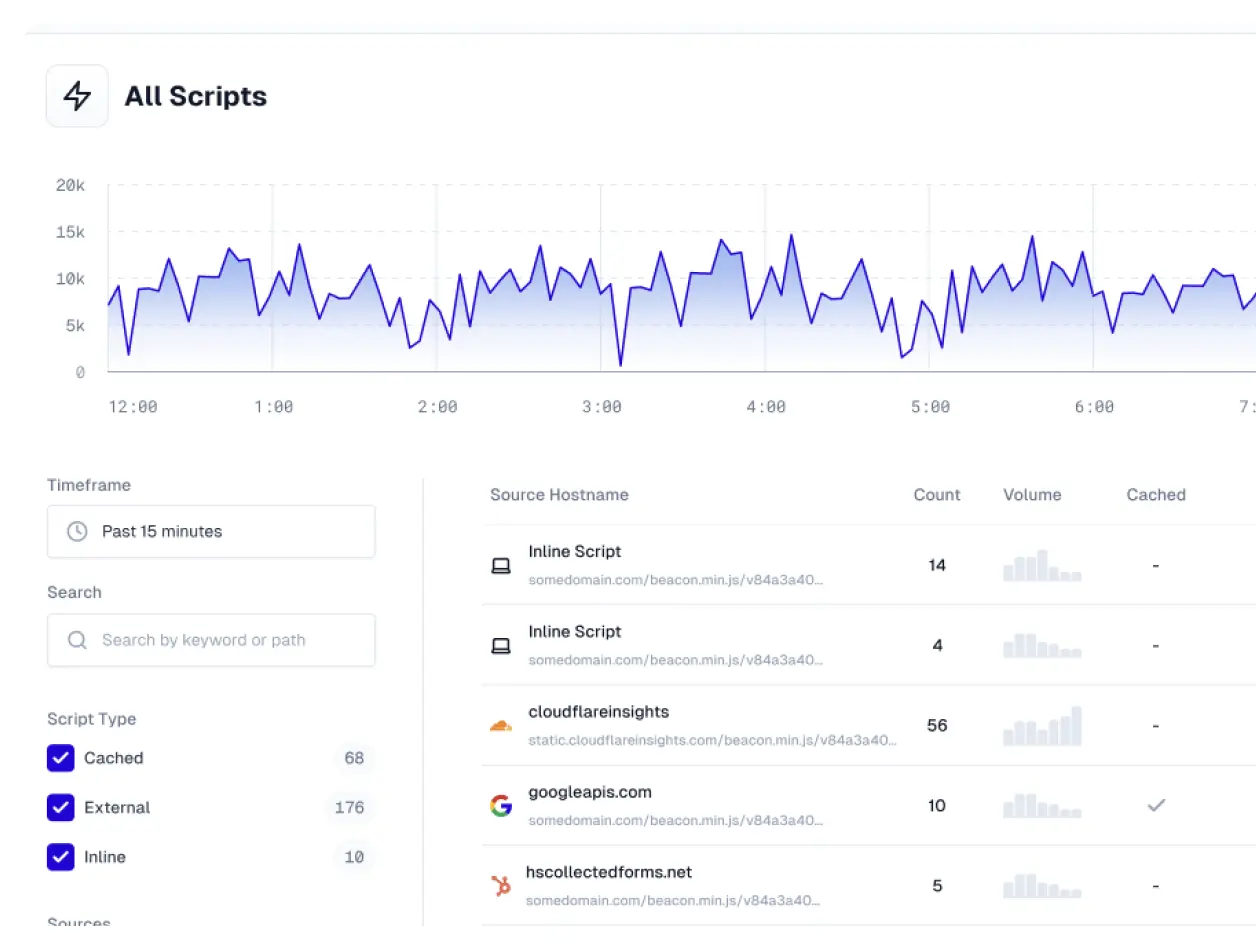
How c/side makes the difference
You'll know what gets delivered to your user's browser 100% of the time, and we'll make the scripts up to 30% faster.
3rd party scripts are a major risk
3rd party scripts have unlimited reign in the browser of your users. When it goes wrong, it goes really wrong.
Negative press, potential lawsuits, and damage claims following a security incident.
You don't know what the user gets in their browser
of most commonly used scripts change at least weekly
3rd-party scripts on
the average website
Know the dangers of
hijacked scripts
It's Time to Take Action
PCI DSS 4.0 (specifically 6.4.3 and 11.6.1) mandates entities handling card data to implement tamper-detection mechanisms by March 31st, 2025. This aims to mitigate Magecart attacks by alerting on unauthorized changes to HTTP headers and payment content.
The value we add
How we're different
- Real time flow-through monitoring
- No sampling, we cover 100%
- Caching scripts, making them faster
- Detection mechanisms that actually work
- Using AI to make findings easily understandable
Detect 0-day attacks
c/side is crawling many sites to get ahead of new attacks. c/side is the only fully autonomous detection tool for assessing 3rd party scripts. We do not rely purely on threat feed intel or easy to circumvent detections. We also use historical context and AI to review the payload and behavior of scripts.
38 million scripts processed in last 24h
All scripts get processed by us to continually enhance our detection capabilities. We monitor over 70 attributes and use various AI-driven techniques to review the scripts, making our solution the most advanced detection system in the space to date.
Works with your favorite stack
Use c/side on your ecommerce store. Whether you use Shopify, Magento, WooCommerce, Next.js, or virtually any front-end. c/side is available to you.
Latest blog posts

Fail Open Architectures: the importance of being ready for a bad day.
Customers diligently ask: “what happens if cside goes down?” or “will it add latency?”. This is how our fail-open architecture is prepared for a bad day.

What QSAs Should Look For When Assessing PCI 6.4.3 and 11.6.1
We put together a shorthand checklist, red flags to look for, and the compliance differences between CSP, Crawlers, and Client-side scripts.

cside Joins AWS Partner Network and ISV Accelerate
Working alongside AWS helps us bring our solution to the cloud environment our customers already rely on. For us, this is a step towards making client-side security widely accessible.






